I’ve known that Azure restricts outbound port 25 within its cloud for security reasons, but today I learned a little more granularity to that.
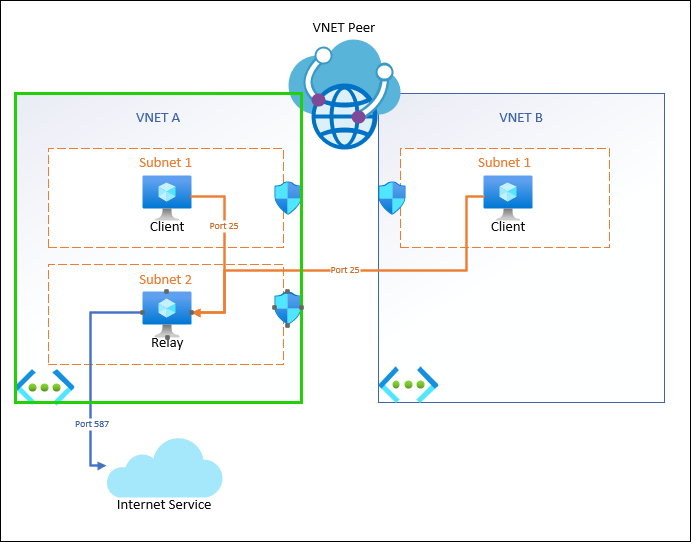
As a baseline, here’s a configuration I’m using in Azure right now, that is functional:
This is two virtual networks, connected with a VNET Peer, with each subnet protected by a Network Security Group allowing port 25 traffic. Clients send un-authenticated SMTP to an internal relay over port 25, and then the relay is configured to send outbound authenticated over port 587 with TLS.
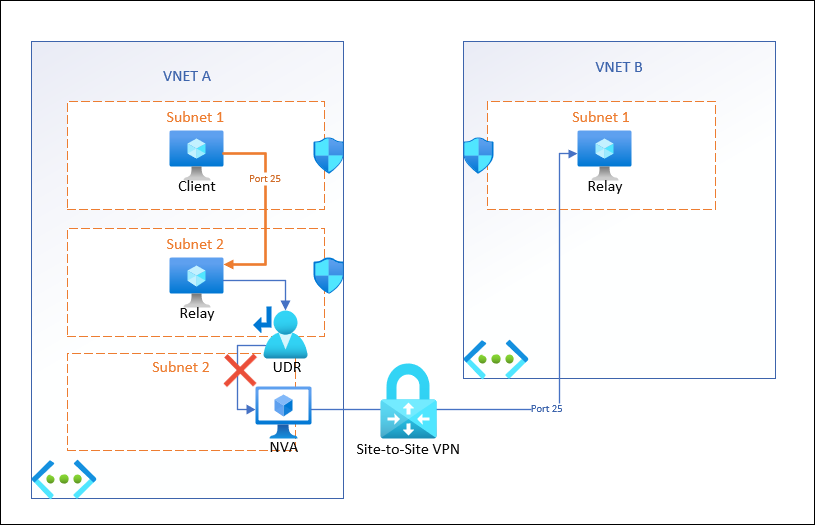
Now here is a configuration that doesn’t work:
This is two virtual networks, connected by a site-to-site VPN tunnel established through a network virtual appliance (in this case, a VeloCloud, but it could be anything).
Then in order to get traffic to the NVA, we use a User-Defined-Route, on a route table, with the NVA LAN interface set as the next hop IP address.
In this scenario, our internal relay is configured to use port 25 to a different relay on the other side of the tunnel.
From what I can tell (because there aren’t diagnostic flow logs like the NSG), the traffic gets blocked at the UDR, because it never hits my NVA. However, other types of traffic (SSH, HTTPS, port 587) have no problem being routed and received.
Its very interesting to me that the native routing of Azure vnets will allow port 25 traffic, but not UDR’s.