My current role has recently expanded to include interaction with Azure, and in this process I came across a permission issue in being able to fully manage Azure AD Application Proxy components.
My administrative account was granted “Co-Administrator” permissions across the Azure subscription by our global team, which was thought to be all that is required to fully managed the components I needed access to.
However, in attempting to set up a new Azure AD Application Proxy, I found that some things were out of place.
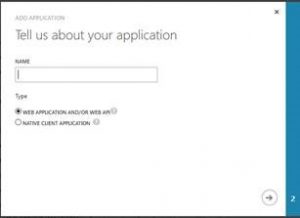
Using the Classic portal, I navigated to the Azure AD application list, and clicked Add. Based on documentation and other’s experience, I expected to see a window posing the “What do you want to do?” question. Instead, I was only give the very next screen for a standard application, “Tell us about your application”:
In troubleshooting this issue, I eventually found that I could not use the new portal (portal.azure.com) to view Enterprise Applications, with an error of “You don’t have access to this data. Please contact your global administrator to get access.”
A bit further research eventually led me to this Azure article regarding user roles within AD: https://azure.microsoft.com/en-us/documentation/articles/active-directory-assign-admin-roles/
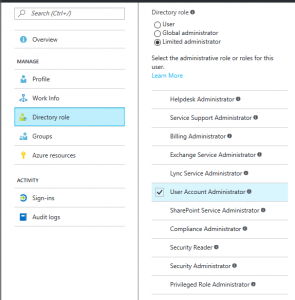
This seemed to be the root of the problem, as when I viewed my administrative user account within Azure AD, it’s Directory Role was listed as a Limited Administrator, with “User Account Administrator” as the granted role:
My global team Changed this to “Global Administrator”, which has opened up the Enterprise Applications blade to me and allowed me to configure Application Proxy. I’m not sure which individual role would also grant the same privileges; perhaps none of them.