After getting a functional script working for deploying an Update Configuration in my last post, I began working on making it worthwhile to use in the future.
I wanted to parameterize the JSON, so that it could be re-used in a much more efficient manner without having to scroll through the file to the JSON body and manually edit sections. This would be needed for both the Subscriptions/ResourceGroups (in the Scope object) and the Tags that I wanted to use.
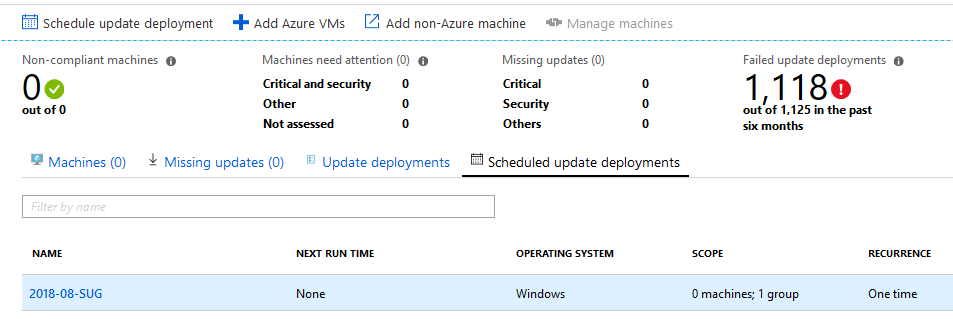
In this example, I wanted a scheduled deployment that ran once (so I could control the date for the first Wednesday after the second Tuesday of the month), with a maintenance window of 4 hours, with dynamic grouping applied against multiple subscriptions and virtual machines with a defined “MaintenanceWindow” tag.
For the Scope definition, I created a PowerShell array containing the resource groups resource IDs. The format of these can be found in the Portal under “Properties” of the resource group.
# Populate this array with the subscription IDs and resource group names that it should apply to $scopeDefinition = @( "/subscriptions/$subscriptionId/resourceGroups/managementVMs" ,"/subscriptions/$subscriptionId/resourceGroups/webVMs" ) |
The Tag definition was created as a Hashtable, noting the tag value that I wanted to include:
# Populate this Hashtable with the tags and tag values that should it should be applied to $tagdefinition = @{ MaintenanceWindow = @("Thurs-2am-MST-4hours") } |
* side note, since Update Management doesn’t operate on the basis of local time of the VM (as SCCM is capable of) I need to build my maintenance windows around discrete time zones, and have multiple update configurations for these time zones even if the local time that I’m targeting is always the same (i.e. 2am).
I can now convert these Powershell variables into JSON:
$applyResourceGroup = $scopeDefinition | ConvertTo-JSON $applyTags = $tagdefinition | ConvertTo-JSON |
and reference it within my JSON body like this:
"targets": { "azureQueries": [{ "scope": $applyResourceGroup, "tagSettings": { "tags": $applyTags, "filterOperator": "Any" }, "locations": null }] } |
Full Example
Here’s a full example that makes parameters of the full contents of the JSON body:
# API Reference: https://docs.microsoft.com/en-us/rest/api/automation/softwareupdateconfigurations/create ### Monthly Parameters ### $deploymentName = "SUG_Thurs-2am-MST-4hours" $starttime = "2018-11-15T02:00:00+00:00" # Scope Parameters $clientsubscription = "<subscription_id_to_target>" # Populate this array with the subscription IDs and resource group names that it should apply to $scopeDefinition = @( "/subscriptions/$clientsubscription/resourceGroups/managementVMs" ,"/subscriptions/$clientsubscription/resourceGroups/webVMs" ) # Static Schedule Parameters $AutomationRG = "test-rg" # Resource Group the Automation Account resides in $automationAccountName = "test-automation" $automationSubscription = "<subscriptionId>" # Subscription that the Automation Account resides in # Populate this Hashtable with the tags and tag values that should it should be applied to $tagdefinition = @{ MaintenanceWindow = @("Thurs-2am-MST-4hours") } $duration = "PT4H0M" # This equals maintenance window - Put in the format PT2H0M, changing the numbers for hours and minutes $rebootSetting = "IfRequired" # Options are Never, IfRequired $includedUpdateClassifications = "Critical,UpdateRollup,Security,Updates" # List of options here: https://docs.microsoft.com/en-us/rest/api/automation/softwareupdateconfigurations/create#windowsupdateclasses $timeZone = "America/Edmonton" # List from ?? $frequency = "OneTime" # Valid values: https://docs.microsoft.com/en-us/rest/api/automation/softwareupdateconfigurations/create#schedulefrequency #$interval = "1" # How often to recur based on the frequency (i.e. if frequency = hourly, and interval = 2, then its every 2 hours) ### These values below shouldn't need to change Select-AzureRmSubscription -Subscription "$automationSubscription" # Ensure PowerShell context is targeting the correct subscription $applyResourceGroup = $scopeDefinition | ConvertTo-JSON $applyTags = $tagdefinition | ConvertTo-JSON # Get the access token from a cached PowerShell session . .\Get-AzureRmCachedAccessToken.ps1 # Source = https://gallery.technet.microsoft.com/scriptcenter/Easily-obtain-AccessToken-3ba6e593 $BearerToken = ('Bearer {0}' -f (Get-AzureRmCachedAccessToken)) $RequestHeader = @{ "Content-Type" = "application/json"; "Authorization" = "$BearerToken" } # JSON formatting to define our required settings $Body = @" { "properties": { "updateConfiguration": { "operatingSystem": "Windows", "duration": "$duration", "windows": { "excludedKbNumbers": [], "includedUpdateClassifications": "$includedUpdateClassifications", "rebootSetting": "$rebootSetting" }, "azureVirtualMachines": [], "targets": { "azureQueries": [{ "scope": $applyResourceGroup, "tagSettings": { "tags": $applyTags, "filterOperator": "Any" }, "locations": null }] } }, "scheduleInfo": { "frequency": "$frequency", "startTime": "$starttime", "timeZone": "$timeZone", "interval": $interval, "isEnabled": true } } } "@ # Build the URI string to call with a PUT $URI = "https://management.azure.com/subscriptions/$($automationSubscription)/" ` +"resourceGroups/$($AutomationRG)/providers/Microsoft.Automation/" ` +"automationAccounts/$($automationaccountname)/softwareUpdateConfigurations/$($deploymentName)?api-version=2017-05-15-preview" # use the API to add the deployment $Response = Invoke-RestMethod -Uri $URI -Method Put -body $body -header $RequestHeader |