Despite being a rather organized person in my professional life, I begin learning new topics and technologies in quite the opposite manner.
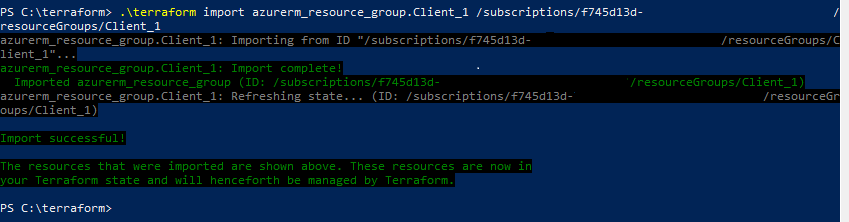
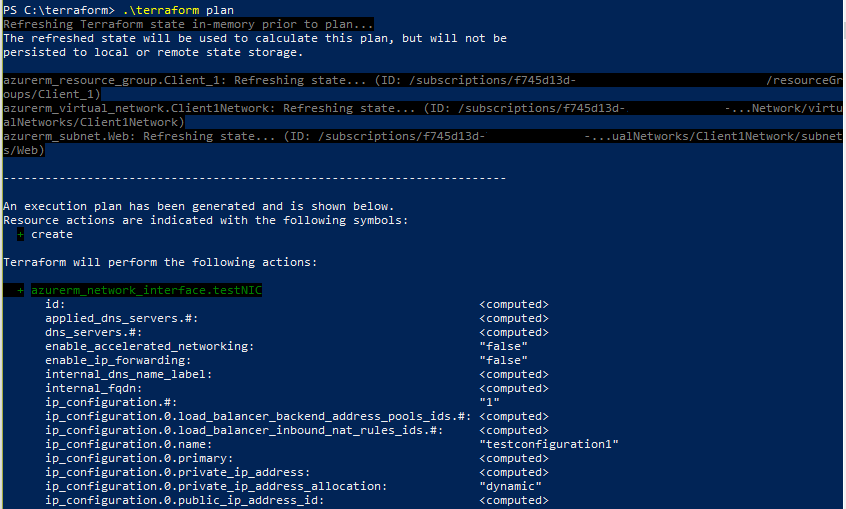
As I begin to dive into Azure automation, today I wanted to understand the proper syntax to deploy small resources with an ARM template while referencing existing resources, rather than what is declared and built within the JSON file itself.
This Azure Quickstart template was very valuable as I spent some time exploring this.
The basic idea:
- Virtual Network and Subnet already exist
- Add Network Interface through ARM template
Once I wrapped my head around the proper way to input the names of existing resource group, virtual network, and subnet, it all kind of clicked for me.
Resource Group is defined during the PowerShell command that calls the JSON file (I’ll show this at the bottom of this post). Parameters are built to accept simple text strings of the virtual network name and subnet name that I’m targeting. Then I used these parameters to build a variable for the subnet, and used that variable in the resource declaration for the network interface.
Here’s the JSON:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 | { "$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json#", "contentVersion": "1.0.0.0", "parameters": { "virtualNetworkName": { "type": "string", "metadata": { "description": "Type existing virtual network name" } } ,"subnetName": { "type": "string", "metadata": { "description": "Type existing Subnet name" } } }, "variables": { ,"subnetRef": "[resourceID('Microsoft.Network/virtualNetworks/subnets', parameters('virtualNetworkName'), parameters('subnetName'))]" }, "resources": [ { "apiVersion": "2015-06-15", "type": "Microsoft.Network/networkInterfaces", "name": "WindowsVM1-NetworkInterface", "location": "[resourceGroup().location]", "tags": { "displayName": "WindowsVM1 Network Interface" }, "properties": { "ipConfigurations": [ { "name": "ipconfig1", "properties": { "privateIPAllocationMethod": "Dynamic", "subnet": { "id": "[variables('subnetRef')]" } } } ] } } ], "outputs": {} } |
New-AzureRmResourceGroupDeployment -ResourceGroupName "Group1" -TemplateFile "C:\Azure\Templates\NewSubnet.json" |