 For a while now I’ve had my Sonicwall Global VPN policy on the firewall set as a “route all” connection. This means that all traffic for the VPN client goes through the Sonicwall directly, and blocks access on the client’s end to local devices.
For a while now I’ve had my Sonicwall Global VPN policy on the firewall set as a “route all” connection. This means that all traffic for the VPN client goes through the Sonicwall directly, and blocks access on the client’s end to local devices.
Yesterday I came upon a situation where I needed to enable a client access to both the VPN and local devices at the same time. This called for Split Tunnels!
However, I didn’t want to enable split tunnels universally for all my VPN clients. Luckily I found this Sonicwall documentation on setting up a single WanGroupVPN with two different policies based on user group.
The premise is that you set up your Wan GroupVPN as a split tunnel, but then give certain users access only to a specific address object and use a specific NAT Policy (I won’t regurgitate the entire document here).
This was working great, but I shortly found that when testing as the split tunnel user, I would get connected and then disconnected within 10 seconds. Typically the connection would last for 3 successful pings.
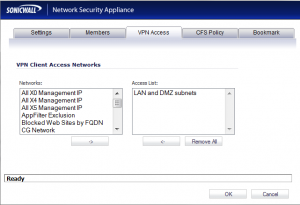
After a bit of Googling I found this article which explained it being caused by an incorrect address object within the “VPN Access” tab for the user.
I checked that out, and strangely enough, only the correct item was listed:
I looked at both the “Everyone” and “Trusted Users” group and it looked the same.
After a lot of head scratching, I finally discovered that in fact the “Everyone” group did have “All Interface IP” object applied to it, by viewing a logged in user’s status here:
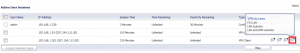
Somehow that was still selected for the “Everyone” group, but it just wasn’t displaying when viewing the “VPN Access” tab. So I clicked “remove all”, and then re-added the appropriate objects, and problem solved!
Interesante tu artículo… pero de qué sirve si no muestras los cambios que hiciste? Pienso que la idea de este post es ayudar a los demás… Creo :V
NOTA: Usa google translator :3