Today I encountered a concerning product limitation of the Azure Application Gateway and Web Application Firewall (WAF) Policies.
Some background first – when working with an Application Gateway v2 sku, you can apply a WAF in 2 different ways:
- Using an in-line WAF policy configuration
- With a WAF Policy object
Microsoft’s documentation appears to be updated to display a preference for using the WAF Policy object, including a scripted method for converting to it: Migrate Web Application Firewall policies using Azure PowerShell
I moved to using a WAF Policy because I wanted to use a series of Terraform local variables to supply WAF rule configuration (exclusions) to both Application Gateway and Azure FrontDoor WAF Policies, without duplicating code.
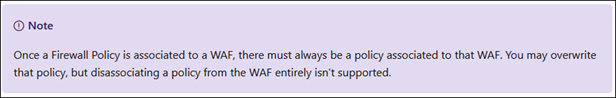
But there is a severe limitation that you may not have noticed in the docs:
You might think, “that’s not a problem, I shouldn’t ever need to disassociate my application gateway” but here’s where it gets wild.
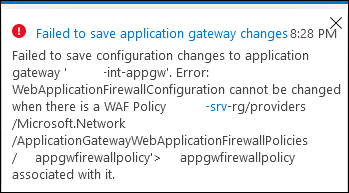
Let’s say that you decide you under-sized your Application Gateway, and want to increase the maximum scale units, or set it to auto-scale. You go to the Configuration blade, and modify the setting, and then hit “save”. You will see this error:
Uh-oh.
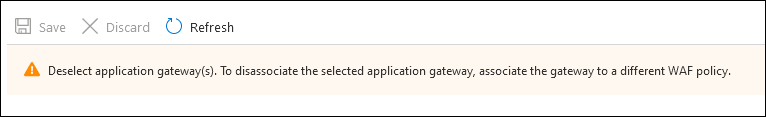
You can try to disassociate the policy in the Portal, but you’ll just see this:
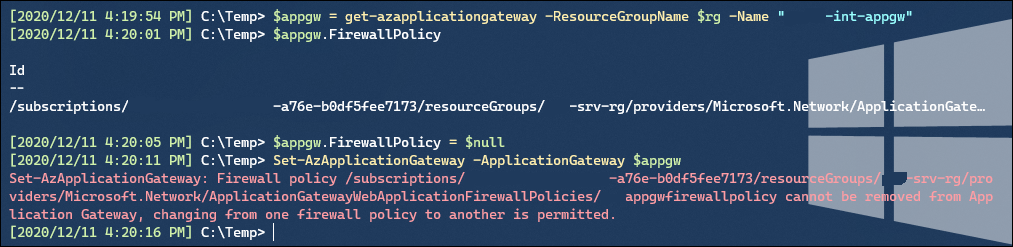
What if we try to disassociate the Policy in PowerShell?
"Firewall policy cannot be removed from Application Gateway, changing from one firewall policy to another is permitted."
This is the limitation – once you’ve applied a WAF Policy, the only way to make a configuration change against the Application Gateway is to destroy it and re-create it. This is absolutely crazy, and means I will not deploy another WAF Policy object until it is resolved. Generally speaking one wouldn’t expect to be changing the AppGw configuration often, but being stuck like this not a good place to be in.
Other’s have talked about this like on ServerFault with a suggestion to shut down the AppGw (not effective) or this issue on azure-cli describing the limitation. To date I haven’t found any viable workaround.
This is a very good post! Thanks
It looks like the error on – configuration save when WAF policy is associated – has been fixed.
Just tried it out. And no error when updating the Application Gateway.
Like Paul has mentioned it seems fixed.